Cross-Site Obtain Forgery (CSRF) can be a type of security vulnerability where a good attacker tricks a user into doing actions on the web application by which they are authenticated. This may lead to illegal actions such because fund transfers, username and password changes, or data exposure. To mitigate CSRF attacks, developers need to carry out robust security techniques. this link describes the best practices regarding preventing CSRF problems.
Understanding CSRF Problems
A CSRF assault occurs when a new malicious website or even script the user’s browser to execute the unwanted action about a trusted web-site for which the particular user is verified. This can end up being attained by exploiting the user’s active period with all the trusted internet site.
Example Scenario:
End user logs into some sort of banking website.
When still logged throughout, the user visits a malicious site.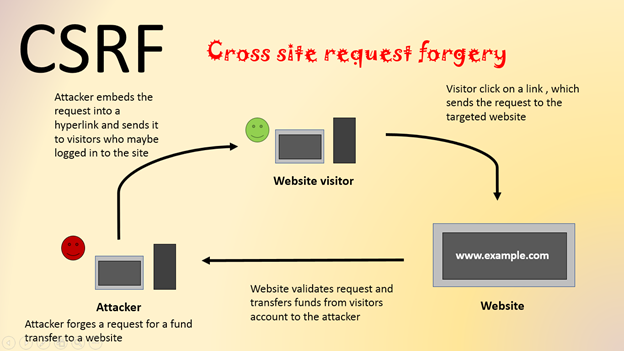
The malicious website sends a ask for to the bank website to shift funds.
The banking website processes typically the request as if it was manufactured by the user, leading to unauthorized dealings.
Best Practices regarding Preventing CSRF Assaults
1. Use Anti-CSRF Tokens
Anti-CSRF tokens are unique beliefs generated by typically the server and integrated in forms or HTTP headers. Whenever a request is created, the server investigations the token to assure it matches the particular expected value. In case the token is definitely missing or wrong, the request is definitely rejected.
Implementation Methods:
Generate a symbol: Typically the server generates a unique token for every user session.
Add the Token in Types: Add the symbol to forms like a hidden field.
Confirm the Token: In receiving a request, the server validates the token.
html
Copy code
python
Copy code
# Flask example
by flask import period, ask for
@app. route(‘/form’, methods=[‘GET’, ‘POST’])
def form():
if request. technique == ‘POST’:
symbol = session. pop(‘_csrf_token’, None)
if not really token or expression! = request. contact form. get(‘_csrf_token’):
abort(403)
return render_template(‘form. html’, csrf_token=session[‘_csrf_token’])
a couple of. Use SameSite Cookie Attribute
The SameSite attribute may be extra to cookies limit them from being sent in cross-origin requests. Setting this specific attribute to Tight or Lax allows prevent CSRF attacks.
Setting SameSite Characteristic:
Strict: Cookies usually are only sent throughout a first-party context but not with requests initiated by thirdparty websites.
Lax: Cookies are sent using top-level navigations and even GET requests initiated by third-party internet sites.
http
Copy signal
Set-Cookie: sessionid=abc123; SameSite=Strict
3. Enable CORS (Cross-Origin Resource Sharing) with Care
CORS policies control which usually external domains can easily access your solutions. Implementing strict CORS policies can reduce CSRF risks.
Steps to Implement CORS:
Designate Allowed Origins: Only allow trusted fields to access your resources.
Set Suitable Headers: Use headers like Access-Control-Allow-Origin to specify allowed roots.
http
Copy signal
Access-Control-Allow-Origin: https://trustedwebsite.com
5. Validate HTTP Referer Header
The HTTP Referer header shows the foundation of the request. Validating this specific header helps to ensure that the request originated from the expected source.
Validation Steps:
Examine the Referer: Ensure typically the Referer header suits your domain.
Decline if Invalid: Reject requests with lacking or mismatched Referer headers.
python
Copy code
@app. route(‘/action’, methods=[‘POST’])
def action():
referer = request. headers. get(‘Referer’)
if not necessarily referer or certainly not referer. startswith(‘https://yourdomain.com’):
abort(403)
# Process the request
5. Implement Secure Coding Procedures
Adopting secure code practices is important with regard to preventing CSRF and other security weaknesses.
Practices to Follow:
Use HTTPS: Make sure all communications usually are encrypted using HTTPS.
Regular Security Audits: Conduct regular safety audits to identify and fix vulnerabilities.
Educate Developers: Train developers on safety best practices plus common vulnerabilities.
6. Monitor and Journal Suspicious Activities
Apply monitoring and logging mechanisms to discover and respond to suspicious activities. This kind of helps in figuring out and mitigating prospective CSRF attacks.
Checking Steps:
Log Asks for: Log all incoming requests, including headers and parameters.
Analyze Logs: Regularly analyze logs for suspicious patterns or particularité.
Alert on Dubious Activities: Established notifications for unusual actions, such as numerous failed CSRF expression validations.
Conclusion
Protecting against CSRF attacks takes a combination of technological measures and safeguarded coding practices. By simply using anti-CSRF bridal party, setting the SameSite cookie attribute, applying strict CORS policies, validating the HTTP Referer header, implementing secure coding procedures, and monitoring with regard to suspicious activities, programmers can significantly decrease the risk associated with CSRF attacks. Staying vigilant and continuously updating security measures is crucial to guard web applications in addition to their users through evolving threats.







Deja una respuesta